Dynamic NAT Configuration on Cisco
This is a Complete article on Dynamic NAT Configuration on Cisco with configuration example. You can find all step by step configuration with Cisco commands in details.While static NAT provides a permanent assignment between an internal local address and an internal global address, dynamic NAT allows automatic assignment of internal local addresses to internal global addresses. Typically, these internal global addresses are public IPv4 addresses. Dynamic NAT uses a group or set of public IPv4 addresses for translation.
Like static NAT, dynamic NAT requires that the internal and external interfaces that participate in NAT be configured. However, while static NAT creates a permanent assignment to a single address, dynamic NAT uses a set of addresses.
Note: Translation between public and private IPv4 addresses is the most frequent use of NAT. However, NAT translations can be performed between any pair of addresses.
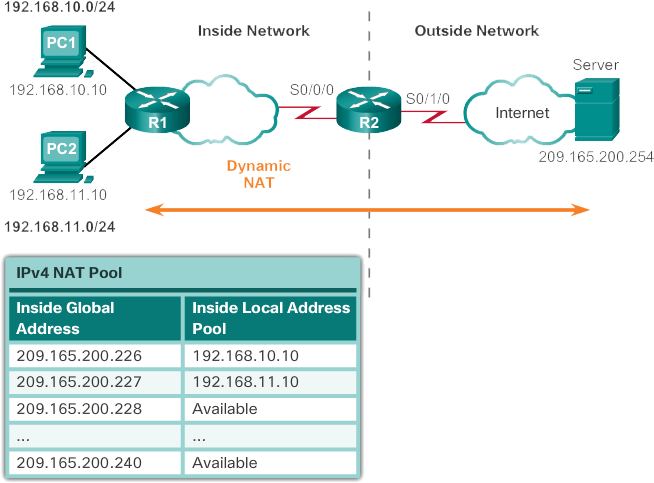
The example topology shown in Image 1 has an internal network that uses addresses from the private address space defined in RFC 1918. There are two LANs connected to router R1: 192.168.10.0/24 and 192.168.11.0/24. Router R2, that is, the border router, was configured for dynamic NAT with a set of public IPv4 addresses from 209.165.200.226 to 209.165.200.240.
The set of public IPv4 addresses (set of internal global addresses) is available for any device in the internal network according to the order of arrival. With dynamic NAT, a single internal address is translated into a single external address. With this type of translation, there must be enough addresses in the set to support all internal devices that need access to the external network at the same time. If all addresses in the set were used, the devices must wait for an address to be available to access the external network.
Steps to configure dynamic NAT on Cisco
The steps and commands used to configure dynamic NAT are shown below.- Step 1: Define the set of addresses that will be used for translation with the ip nat pool command . Usually, this set is a group of public addresses. The addresses are defined indicating the first and last IPv4 address of the set. The netmask or prefix-length keywords indicate which address bits belong to the network and which ones to the host in the address range.
- Step 2: Configure a standard ACL to identify (allow) only those addresses that must be translated. An ACL that is too permissive can generate unpredictable results. Remember that at the end of each ACL there is an implicit instruction to deny everything .
- Step 3: Connect the ACL to the assembly. The ip nat inside source list access-list-number pool name set name is used to link the ACL to the set. The router uses this configuration to determine which address ( pool ) each device receives ( list ).
- Step 4: Identify which interfaces are internal with respect to NAT; that is, any interface that connects to the internal network.
interface type
ip number nat inside
- Step 5: Identify which interfaces are external with respect to NAT; that is, any interface that connects to the external network.
interface type
ip number nat outside
Example of dynamic NAT configuration
In Image 2, a topology and an example configuration are shown. This configuration allows translation for all hosts in the 192.168.0.0/16 network, which includes the 192.168.10.0 and 192.168.11.0 LANs, when they generate traffic that enters through S0 / 0/0 and leaves through S0 / 1/0. These hosts are translated to an available address of the set in the range of 209.165.200.226 to 209.165.200.240.Define a set of public IPv4 addresses with the set name NAT-POOL1.
R2 (config) # <b> ip nat pool NAT-POOL1 209.165.200.226
209.165.200.240 netmask 255.255.255.224
Define the addresses that can be translated.
R2 (config) # access-list 1 permit 192.168.0.0 0.0.255.255
Connect NAT-POOL1 to ACL 1.
R2 (config) # <b> ip nat inside source list 1 pool NAT-POOL1
Identify the 0/0/0 serial interface as an internal NAT interface.
R2 (config) # interface Serial0 / 0/0
R2 (config-if) # ip nat inside
Identify the serial interface 0/1/0 as an external NAT interface.
R2 (config) # interface Serial0 / 1/0
R2 (config-if) # ip nat outside
DYNAMIC NAT PROCESS
With the previous configuration, the illustrations show the dynamic NAT translation process between two clients and the web server:INSIDE OUT
- 1 . The hosts with the source IPv4 addresses (PC1 and PC2) send packets to request connection to the server at the public IPv4 address (209.165.200.254).
- 2 . R2 receives the first host package 192.168.10.10. Because this package was received on an interface configured as an internal NAT interface, R2 verifies the NAT configuration to determine if this package should be translated. As the ACL allows this package, R2 translates it. R2 consults its NAT table. Because there is no translation entry for this IPv4 address, R2 determines that the source address 192.168.10.10 must be translated dynamically. R2 selects an available global address from the dynamic address set and creates a translation entry, 209.165.200.226. The initial source IPv4 address (192.168.10.10) is the internal local address, and the translated address is the internal global address (209.165.200.226) in the NAT table.
For the second host, 192.168.11.10, the R2 repeats the procedure, selects the next available global address from the dynamic address set and creates a second translation entry, 209.165.200.227.
- 3 . R2 replaces the internal local source address of PC1, 192.168.10.10, with the translated internal global address 209.165.200.226 and resends the packet. The same process is carried out for the PC2 package with the address translated for this computer (209.165.200.227).
FROM THE OUTSIDE IN
- 4 . The server receives the packet from PC1 and responds with the destination IPv4 address 209.165.200.226. When the server receives the second packet, it responds to PC2 with the destination IPv4 address 209.165.200.227.
- 5th . When R2 receives the packet with destination IPv4 address 209.165.200.226, it performs a search in the NAT table. With the assignment of the table, R2 translates the address back to the internal local address (192.168.10.10) and forwards the packet to PC1.
- 5b . When R2 receives the packet with the destination IPv4 address 209.165.200.227, it performs a search in the NAT table. With the assignment of the table, R2 translates the address back to the internal local address (192.168.11.10) and forwards the packet to PC2.
- 6 . PC1 and PC2 receive the packets and continue the conversation. The router performs steps 2 through 5 for each packet. (Step 6 does not appear in the illustrations).
STATIC NAT VERIFICATION
The result of the show ip nat translations command below, shows the details of the two previous NAT assignments. The command shows all static translations that were configured and all dynamic translations that were created because of traffic.R2 # show ip nat translations
Pro Inside global Inside local Outside local Outside global
--- 209.165.200.226 192.168.10.10 --- ---
--- 209.165.200.227 192.168.11.10 --- ---
R2 #
R2 # show ip nat translations verbose
Pro Inside global Inside local Outside local Outside global
--- 209.165.200.226 192.168.10.10 --- ---
create 00:17:25, use 00:01:54 timeout: 86400000, left
23:58:05, Map-Id (In): 1,
flags:
none, use_count: 0, entry-id: 32, lc_entries: 0
--- 209.165.200.227 192.168.11.10 --- ---
create 00:17:22, use 00:01:51 timeout: 86400000, left
23:58:08, Map-Id (In): 1,
flags:
none, use_count: 0, entry-id: 34, lc_entries: 0
R2 #
If the verbose keyword is added , additional information about each translation is displayed, including the time elapsed since the entry was created and the entry was used.By default, translation entries expire after 24 hours, unless the timers have been reconfigured with the ip nat translation timeout timeout -seconds command in global configuration mode.
DELETE DYNAMIC ENTRIES
To clear dynamic entries before timeout, use the clear ip nat translation command in EXEC mode with privileges. It is useful to delete dynamic entries when testing the NAT configuration. As shown in the table, this command can be used with keywords and variables to control which entries should be deleted. You can delete specific entries to avoid interrupting active sessions. Use the clear ip nat translation * command in EXEC mode with privileges to delete all translations from the table.R2 # clear ip nat translation *
R2 # show ip nat translations
R2 #
| Command | Description |
|---|---|
| clear ip nat translation * | Remove all dynamic address translation entries from the NAT translation table. |
| clear ip nat translation inside ip-global ip-local [ outside ip-local ip-global ] | Deletes a simple dynamic translation entry that contains an internal translation or an internal and external translation. |
| clear ip nat translation protocol inside ip-global global-port ip-local local-port [ outside ip-local local port ip-global global-port ] |
R2 # clear ip nat statistics
PC1 and PC2 establish sessions with the server
R2 # show ip nat statistics
Total active translations: 2 (0 static, 2 dynamic; 0 extended)
Peak translations: 6, occurred 00:27:07 Aug
Outside interfaces:
Serial0 / 0/1
Inside interfaces:
Serial0 / 1/0
Hits: 24 Misses: 0
CEF Translated packets: 24, CEF Punted packets: 0
Expired translations: 4
Dynamic mappings:
- Inside Source
[Id: 1] access-list 1 pool NAT-POOL1 refcount 2
pool NAT-POOL1 : netmask 255.255.255.224
start 209.165.200.226 end 209.165.200.240
type generic, total addresses 15, allocated 2 (13%), misses 0
Total doors: 0
Appl doors: 0
Normal doors: 0
Queued Packets: 0
R2 #
You can also use the show running-config command and search for the NAT, ACL, interface or set commands with the required values. Examine them carefully and correct any errors you detect.



No comments:
Post a Comment