Cisco Network Protocols and Standard Related to CCNA
This article is a brief introduction of Cisco Network Protocols and Standard Related to CCNA. After reading this article you will have a clear understanding of network communication rules. This will clear the basic concepts to understanding the further CCNA topics.
The networks are based on human communication, and that simply making the physical wired or wireless connection between the terminals is not enough to enable communication. For communication to occur, devices must know how to communicate.
What is a Protocol?
All communication methods have three elements sender, channel and receiver. The sending of a message, either through face to face communication or through a network, is governed by rules called " protocols ", these being specific to the type of communication method in question. The protocols used in network communications, in addition to identifying the origin and destination, define details about the way in which messages are transmitted through a network.
NETWORK COMMUNICATION RULES
All communication in network is perform through packets or messages, following term provide you the basic concept of a network message:
- Message Encoding
- Message format and encapsulation
- Message size
- Message Synchronization
- Message delivery options
MESSAGE ENCODING
Coding is the process of converting information into another form acceptable for transmission. Decoding reverses this process to interpret the idea. Each bit is encoded in a pattern of sounds, light waves or electronic impulses, depending on the medium through which the bits are transmitted. The destination host receives and decodes the signals to interpret the message.
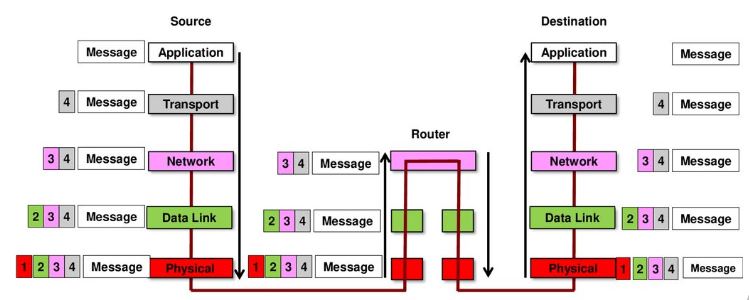
MESSAGE FORMAT AND ENCAPSULATION
The process of placing a message format (for example, a letter) into another message format (the envelope) is called encapsulation . When the recipient reverses this process and removes the letter from the envelope, the decapsulation occurs. Each computer message is encapsulated in a specific format, called a frame (the envelope in the letter example), before being sent over the network.
MESSAGE SIZE
Frame size restrictions require the source host to divide a long message into individual fragments that meet the minimum and maximum size requirements. The long message will be sent in independent frames, each frame will contain a part of the original message. Each frame will also have its own addressing information. On the receiving host, the messages are decapsulated and rejoined for processing and interpretation.
MESSAGE SYNCHRONIZATION
The three elements are taken into account: Access method, Flow control and Timeout for the response. The Access Method determines when a device can send a message; the flow control determines the amount of information that can be sent and the speed with which it can be delivered and; The Timeout for the response specifies how long they should wait for an answer and what to do if it runs out.
MESSAGE DELIVERY OPTIONS
A message can be delivered in different ways:
- Unicast (Multicast)
- Multicast (Multicast)
- Broadcast (Broadcast)
A one-to-one delivery option is called "unicast," which means that the message has only one recipient. If a host needs to send messages to several at the same time, it is called "multicasting." If it is necessary for all hosts on the network to receive the message at the same time, the broadcast method is used.
Cisco NETWORK PROTOCOLS
The protocols define the format and structure of the message that the devices exchange. Some examples of the most common network protocols are Hypertext Transfer Protocol (HTTP), the transmission control protocol (TCP) and the Internet protocol (IP).
TCP / IP PROTOCOL SUITE or Model
TCP / IP protocols are specific to the Application, Transport and Internet layers . The protocols of the network access layer are responsible for the delivery of IP packets on physical media and are developed by standardization organizations, such as IEEE.
Table of the TCP / IP Protocol Set.
| Protocol | Description |
|---|
| DNS | Translate domain names such as ccnacompletecourse.blogspot.com to an IP addresses |
| DHCP | Assign IP addresses dynamically to counting stations when started and allow addresses to be reused when they are no longer needed |
| BOOTP | Enable a diskless workstation to discover its own IP address, the IP address of a BOOTP server on the network and a file that must be loaded into memory to start the machine. |
| IMAP | Allows customers to access emails stored on a mail server |
| POP | Allows customers to retrieve an email from a mail server |
| SMTP | Allow customers to send an email to a mail server |
| FTP | Sets the rules that allow a user on a host to access and transfer files to and from another host on a network |
| TFTP | A file delivery protocol without acknowledgment of great effort that uses less overhead than FTP. |
| HTTP | Set of rules for exchanging text, graphic images, sound, video and other multimedia files on the World Wide Web |
| UDP | Enable a process that runs on one host to send packets to a process that runs on another host |
| TCP | It allows reliable communication between processes running on independent hosts |
| IP | Route packages for complete training through an intemetwork |
| NAT | Translate IP addresses from a private network to unique public IP addresses globally |
| ICMP | Provide comments from a destination host to a source host regarding packet delivery errors |
| OSPF | Link-State Routing Protocol |
| EIGRP | Cisco Exclusive Routing Protocol |
| ARP | Provides dynamic address assignment between an IP address and a hardware address |
| PPP | It provides a means of encapsulating packets to transmit them through a serial link |
| Ethernet | Define the rules for connecting and signaling network access layer standards |
| Internet controllers | Provides instructions to the machine to control a specific interface on a network device
|
NETWORK STANDARDS ORGANIZATIONS
Open standards ensure that no single company product can monopolize the market or have an unfair advantage over the competition. For example, they allow a client with the Apple OS X operating system to download a web page from a web server with the Linux operating system. This is because both operating systems implement the open standard protocols, such as those in the TCP / IP suite.
INTERNET STANDARDS
Different organizations have different responsibilities to promote and develop standards for the TCP / IP protocol. With regard to the Internet we have:
- Internet Engineering Working Group (IEFT) : develops, updates and maintains Internet and TCP / IP technologies. This includes documentation for the development of new protocols and the updating of existing protocols, known as comment request documents (RFCs).
- Internet Society (ISOC) : is responsible for promoting the open development, evolution and use of the Internet worldwide.
- Internet Corporation for Assigned Names and Numbers (ICANN) : based in the United States, it coordinates the assignment of IP addresses, the administration of domain names and the assignment of other information used by the TCP / IP protocols.
- Internet Architecture Council (IAB) : is responsible for the administration and general development of Internet standards.
- Internet Research Working Group (IRTF) : is focused on long-term research in relation to Internet and TCO / IP protocols.
- Internet Assigned Numbers Authority (IANA) : responsible for supervising and administering IP address assignment, domain name management and protocol identifiers for ICANN.
ORGANIZATIONS OF STANDARDS FOR COMMUNICATIONS AND ELECTRONICS
They have responsibilities for the promotion and creation of standards that are used in the delivery of IP packets such as electronic signals in wireless or cable media. And we have:
- Institute of Electrical and Electronics Engineers (IEEE) : Dedicated to advancing technological innovation and developing standards in a wide range of sectors, including energy, health services, telecommunications and networks.
- Electronic Industries Association (EIA) : standards related to electrical wiring, connectors and racks 19.
- Association of Telecommunications Industries (TIA) : communication standards including radio equipment, mobile phone towers, voice over IP (VoIP) devices, satellite communications and more.
- Telecommunication Standardization Sector of the International Telecommunication Union (ITU-T) : Defines standards for video compression, Internet protocol television (IPTV) and broadband communications, such as the digital subscriber line (DSL).
- Among some known standards we have IEEE 802.3 , which defines the media access control (MAC) for wired Ethernet and IEEE 802.11 , which defines a set of standards for implementing wireless local area networks (WLAN).
I hope this informative for your, thank you for visiting here.!