Access Control List Cisco ACL Rules
Here you will learn the purpose & guidelines for the creation & placement of Access Control List Cisco in order to provide security to a network are explained . In the last part of post you will see Cisco ACL Rules.One of the most important skills a network administrator needs is the domain of access control lists (ACLs). Network designers use firewalls to protect networks from unauthorized use. Firewalls are hardware or software solutions that enforce network security policies and filter unauthorized or potentially dangerous packets and prevent them from entering the network. On a Cisco router , you can configure a simple firewall that provides basic traffic filtering capabilities through ACL . Administrators use ACLs to stop traffic or to allow only specific traffic on their networks.
Contents of this Article
1. What is the access control list?
2. Filtering packages
3. Operation of the ACLs
4. Wildcard masks in ACL
5. Guidelines for the creation of ACL
6. Guidelines for the placement of ACL
What is the access control list Cisco?
An ACL is a series of IOS commands that control whether a router forwards or discards packets based on the information found in the packet header. ACLs are one of the most used features of Cisco IOS software.
ACL TASKS
When configured, ACLs perform the following tasks:
- They limit network traffic to increase their performance . For example, if corporate policy does not allow video traffic on the network, ACLs that block video traffic can be configured and applied. This would significantly reduce the network load and increase its performance.
- They provide traffic flow control . ACLs can restrict the delivery of routing updates to ensure that the updates come from a known source.
- They provide a basic level of security for network access . ACLs can allow one host to access a part of the network and prevent another host from accessing the same area.
- They filter the traffic according to the type of traffic . For example, an ACL can allow email traffic, but block all Telnet traffic.
- They filter hosts to allow or deny them access to network services . ACLs can allow or deny users access to certain types of files, such as FTP or HTTP.
FILTERING PACKAGES
An ACL is a sequential list of permit (allow) or deny (deny) instructions , known as “ access control entries ” (ACE). ACEs are also commonly referred to as "ACL instructions." When the network traffic crosses an interface configured with an ACL, the router compares the information within the packet with each ACE, in sequential order, to determine if the packet matches one of the ACEs. This process is called packet filtering .
Standard ACLs filter only in Layer 3. Extended ACLs filter in layers 3 and 4.
The filtering criteria established in each ACE of a standard IPv4 ACL is the source IPv4 address. A router configured with a standard IPv4 ACL retrieves the source IPv4 address of the packet header. The router starts at the top of the ACL and compares the address with each ACE sequentially. When it finds a match, the router performs the instruction, which may be to allow or deny the packet. Once a match is found, the remaining ACEs of the ACL, if any, are not analyzed. If the source IPv4 address does not match any ACE in the ACL, the packet is discarded.
The last instruction of an ACL is always an implicit denial. This statement is automatically inserted at the end of each ACL, even if it is not physically present. Implicit denial blocks all traffic. Due to this implicit denial, an ACL that does not have at least one permit instruction will block all traffic .
Operation of the ACLs
Access Control Lists define the set of rules that provide additional control for packets that enter through the input interfaces, for those that relay through the router, and for those that exit through the router's output interfaces. ACLs do not operate on packets that originate from the router itself.- Inbound ACL: Incoming packets are processed before routing to the outgoing interface. Inbound ACLs are effective, because they save the overhead of routing searches if the packet is dropped. If ACLs allow the packet, it is processed for routing. The input ACLs are ideal for filtering packets when the network connected to an input interface is the only source of the packets to be examined.
- Outbound ACL: Inbound packets are routed to the outbound interface and then processed through the outbound ACL. Output ACLs are ideal when the same filter is applied to packets that come from several input interfaces before leaving through the same output interface
Wildcard masks in ACL
IPv4 ACEs include the use of wildcard masks. A wildcard mask is a 32-bit binary string that the router uses to determine which bits of the address it must examine to obtain a match.As with subnet masks, numbers 1 and 0 in the wildcard mask identify what needs to be done with the corresponding IPv4 address bits. However, in a wildcard mask, these bits are used for different purposes and follow different rules.
While subnet masks use binary ones and zeros to identify the network, subnet and host portion of an IPv4 address; wildcard masks use binary ones and zeros to filter individual IPv4 addresses or groups of IPv4 addresses to allow or deny access to resources.
Wildcard masks and subnet masks differ in the way they match binary ones and zeros. The first, use the following rules to establish the match between ones and binary zeros:
- Wildcard mask bit 0: the match is set with the corresponding bit value in the address.
- Wildcard mask bit 1 : the value of the corresponding bit in the address is omitted.
Wildcard masks are often referred to as " reverse masks s". The reason is that, unlike a subnet mask in which the binary 1 is equivalent to a match and the binary 0 is not a coincidence, in wildcard masks it is the other way around.
USE OF A WILDCARD MASK
In Image 4, the results of the application of a wildcard mask 0.0.255.255 to a 32-bit IPv4 address are shown. Remember that a binary 0 indicates a value that matches.Note : Unlike IPv4 ACLs, IPv6 ACLs do not use wildcard masks. Instead, the prefix length is used to indicate how much of a source or destination IPv6 address must match.
EXAMPLES OF WILDCARD MASK
It takes practice to calculate the wildcard mask. In Image 5, three examples of wildcard mask are provided.- In the first example, the wildcard mask stipulates that each bit in IPv4 192.168.1.1 must match exactly.
- For the second example, the wildcard mask stipulates that there will be no matches.
- In the third example, the wildcard mask stipulates that any host within the 192.168.1.0/24 network will have a match.
WILDCARD MASK CALCULATION
Calculating wildcard masks can be difficult. A shortcut is to subtract the subnet mask from 255.255.255.255.WILDCARD MASK CALCULATION: EXAMPLE 1
In the first example in the illustration, suppose you want to allow access to all users on the 192.168.3.0 network. Since the subnet mask is 255.255.255.0, it could take 255.255.255.255 and subtract the subnet mask 255.255.255.0. The result generates the wildcard mask 0.0.0.255.
WILDCARD MASK CALCULATION: EXAMPLE 2
In the second example in the illustration, suppose you want to allow the 14 users to access the network on the 192.168.3.32/28 subnet. The subnet mask for the IPv4 subnet is 255.255.255.240; therefore, take 255.255.255.255 and subtract the subnet mask 255.255.255.240. This time, the result generates the wildcard mask 0.0.0.15.
You can achieve the same result with instructions such as the two shown below:
R1 (config) # access-list 10 permit 192.168.10.0
R1 (config) # access-list 10 permit 192.168.11.0
It is much more efficient to configure the wildcard mask as follows:
R1 (config) # access-list 10 permit 192.168.10.0 0.0.1.255
Consider an example in which networks should be matched in the range of 192.168.16.0/24 to 192.168.31.0/24. These networks will summarize in 192.168.16.0/20. In this case, 0.0.15.255 is the correct wildcard mask to configure an effective ACL declaration, as shown below:
R1 (config) # access-list 10 permit 192.168.16.0 0.0.15.255
KEYWORDS OF WILDCARD MASKS: EXAMPLES
Working with decimal representations of the binary bits of wildcard masks can be tedious. To simplify this task, the keywords host and any help identify the most common uses of wildcard masks. These keywords eliminate the need to enter wildcard masks to identify a specific host or an entire network. They also facilitate the reading of an ACL, as they provide visual clues as to the origin or destination of the criteria.- The host keyword replaces the 0.0.0.0 mask. This mask indicates that all bits of IPv4 addresses must match to filter only one host address.
- The any option replaces the IP address and mask 255.255.255.255. This mask states that the full IPv4 address is omitted or that any address is accepted.
Example 1: wildcard mask process with a single IPv4 address
In example 1 in the illustration, instead of entering 192.168.10.10 0.0.0.0 , you can use host 192.168.10.10 .
Below is how to use the keyword any to replace the IPv4 address 0.0.0.0 with a 255.255.255.255 wildcard mask.
R1 (config) # access-list 1 allow 0.0.0.0 255.255.255.255
! OR <br>
R1 (config) # access-list 1 permit any
Example 2: wildcard mask process matching any IPv4 address
In Example 2 in the illustration, instead of entering 0.0.0.0 255.255.255.255 , you can use the keyword any (any) alone.
Below is how to use the host keyword to replace the wildcard mask to identify a single host.
R1 (config) # access-list 1 permit 192.168.10.10 0.0.0.0
! OR <br>
R1 (config) # access-list 1 permit host 192.168.10.10
Guidelines for the creation of ACL
The composition of ACL can be a complex task. For each interface, there may be several policies necessary to manage the type of traffic that is allowed to enter or exit the interface. The router in the illustration has two interfaces configured for IPv4 and IPv6. If we needed ACLs for both protocols, on both interfaces and both ways, this would require eight different ACLs. Each interface would have four ACLs: two ACLs for IPv4 and two ACLs for IPv6. For each protocol, one ACL is for inbound traffic and another for outbound traffic.Note: ACLs must not be configured both ways. The amount of ACL and the meaning applied to the interface depend on the requirements that are implemented.
The following are some guidelines for the use of ACL:
- Use ACLs on firewall routers located between your internal network and an external network, such as the Internet.
- Use ACLs on a router located between two parts of the network to control traffic that enters or leaves a specific part of your internal network.
- Configure ACLs on border routers, that is, routers located in the boundaries of networks. This provides a very basic separation of the external network or between a less controlled area and a more important area of your own network.
- Configure the ACLs for each network protocol configured on the border router interfaces.
RULES FOR APPLYING ACLS
An ACL can be configured per protocol, per direction and per interface:- One ACL per protocol: to control the flow of traffic on an interface, an ACL must be defined for each protocol enabled on the interface. (e.g., IPv4 or IPv6)
- One ACL per direction: ACLs control traffic on an one-way interface at a time. Two different ACLs must be created to control incoming and outgoing traffic. (i.e. inbound or outbound)
- One ACL per interface: ACLs control traffic for an interface, for example, GigabitEthernet 0/0.
ACL OPTIMIZATIONS
The use of ACLs requires attention to detail and extreme care. Errors can be costly in terms of downtime, problem solving efforts and poor network service. Before configuring an ACL, basic planning is required. The following table presents guidelines that form the basis of a list of recommended practices for ACL.
Guidelines
|
Advantages
|
Basically its ACL
according to the organization's security policies.
|
This will ensure the
implementation of the organization's safety guidelines.
|
Prepare a description of
what you want the ACLs to do.
|
This will help you avoid
possible access problems generated inadvertently.
|
Use a text editor to
create, edit and save ACLs.
|
This will help you create
a reusable ACL library.
|
Test your ACLs in a
development network before implementing them in a production network.
|
This will help you avoid
costly mistakes.
|
ACL Optimization Table.
|
|
Guidelines for the placement of ACL
The correct placement of ACLs can help the network to function more efficiently. An ACL can be placed to reduce unnecessary traffic. For example, traffic that will be denied at a remote destination should not be forwarded via network resources along the route to that destination.
The placement of the ACL and, therefore, the type of ACL used may also depend on the following:
Scope of network administrator control: The placement of the ACL may depend on whether the network administrator controls both the source and destination networks or not.
Bandwidth of the networks involved: the filtering of unwanted traffic at the source prevents the transmission of that traffic before it consumes bandwidth on the route to a destination. This is especially important in networks with low bandwidth.
Ease of configuration: if a network administrator wishes to deny traffic coming from several networks, one option is to use a single standard ACL on the router closest to the destination. The disadvantage is that traffic from such networks will use bandwidth unnecessarily. An extended ACL can be used on each router where traffic originates. This saves bandwidth, since traffic is filtered at the source, but requires the creation of extended ACLs on several routers.
WHERE TO LOCATE ACLS
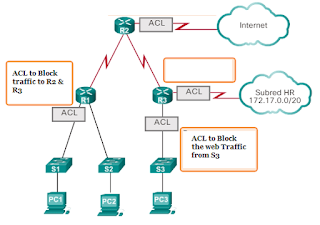
Each ACL should be placed where it has the greatest impact on efficiency. As shown in Image 12, the basic rules are as follows:- Extended ACLs: place extended ACLs as close as possible to the source of the traffic to be filtered. In this way, unwanted traffic is denied near the home network, without crossing the network infrastructure.
- Standard ACL: Because the standard ACLs do not specify the destination addresses, place them as close to the destination as possible. If you place a standard ACL at the source of the traffic, it will effectively prevent that traffic from reaching any other network through the interface to which the ACL applies.
Note : Although extended ACLs are outside the scope of the ICND1 / CCENT exam, you should know the general guidelines for placing both standard and extended ACLs.
For CCNA certification, the general rule is that extended ACLs be placed as close as possible to the origin and that standard ACLs be placed as close as possible to the destination.
LOCATION OF THE STANDARD ACL
The topology in Image 13 is used to demonstrate how a standard ACL can be positioned. The administrator wishes to prevent traffic originating from the 192.168.10.0/24 network from reaching the 192.168.30.0/24 network.In accordance with the basic standard ACL placement guidelines near the destination, the illustration shows two possible R3 interfaces to which to apply the standard ACL:
- Interface S0 / 0/1 of R3: the application of a standard ACL to prevent 192.168.10.0/24 traffic from entering the S0 / 0/1 interface prevents such traffic from reaching 192.168.30.0/24 and the rest of the the networks that R3 can reach. This includes the 192.168.31.0/24 network. Since the purpose of the ACL is to filter traffic destined only to 192.168.30.0/24, a standard ACL should not be applied to this interface.
- G0 / 0 interface of R3: when applying a standard ACL to the traffic that leaves through the G0 / 0 interface, packets ranging from 192.168.10.0/24 to 192.168.30.0/24 are filtered. This does not affect the other networks that R3 can reach. 192.168.10.0/24 packages can still reach 192.168.31.0/24.






No comments:
Post a Comment