CSMA / CA & Wireless Network Operation
This article is about CSMA / CA & Wireless Network Operation serial of wireless WLAN, in previous article was about 802.11 Frame Structure Wireless. Remember that the media contention method is the method by which devices determine how and when to access the media when traffic is to be forwarded through the network. IEEE 802.11 WLANs use the CSMA / CA MAC protocol . While the name is similar to that of the Ethernet Carrier Sense Multiple Access with Collision Avoidance CSMA / CD method, the operational concept is completely different.CSMA / CA Carrier Sense Multiple Access with Collision Avoidance
Wi-Fi systems are half-duplex shared media configurations; therefore, wireless clients can transmit and receive on the same radio channel.This creates a problem, since a wireless client cannot hear while sending; therefore, it is not possible to detect a collision. To address this problem, IEEE developed an additional mechanism for collision prevention called “ distributed coordination function ” (DCF).
Through DCF, a wireless client transmits only if the channel is free. All transmissions are confirmed; Therefore, if a wireless client does not receive an acknowledgment, it assumes that a collision occurred and tries again after a random waiting interval.
Wireless clients and APs use the RTS and CTS control frames to facilitate the transfer of data itself.
- As shown in above figure, when a wireless client sends data, it first evaluates the means to determine if other devices are using them to transmit.
- Otherwise, it sends an RTS frame to the AP.
- This frame is used to request dedicated access to the RF medium during a specific period.
- The AP receives the frame and, if available, grants the wireless client access to the RF medium by sending a CTS frame of the same duration.
- All other wireless devices that observe the CTS frame transfer the media to the transmitting node for transmission.
- The CTS control frame includes the period during which it is allowed to transmit to the transmitting node. Other wireless clients retain transmissions for at least the specified period.
Association of access points and wireless clients
For wireless devices to communicate over a network, they must first be associated with an AP or a wireless router. An important part of the 802.11 process is to discover a WLAN and connect to it.
Wireless devices use management frames to complete the following three-stage process:
- Discover new wireless APs.
- Authenticate with the AP.
- Join the AP.
To associate, a wireless client and an AP must agree on specific parameters. To allow the negotiation of these processes, the parameters must be configured in the AP and later in the client.
Association Parameters of Wireless Network
Common configurable wireless parameters include the following:- SSID : An SSID is a unique identifier that wireless clients use to distinguish between several wireless networks in the same area.
- The name of the SSID appears in the list of wireless networks available on a client. Depending on the network configuration, several APs in a network can share an SSID. In general, names have a length of 2 to 32 characters.
- Password : The wireless client needs it to authenticate with the AP. Passwords are sometimes called a "security key." Prevents intruders and other unwanted users from accessing the wireless network.
- Network mode : refers to the WLAN 802.11a / b / g / n / ac / ad standards. APs and wireless routers can operate in Mixed mode, which means they can use several standards at once.
- Security mode : refers to the configuration of security parameters, such as WEP, WPA or WPA2. Always enable the highest level of security that is supported.
- Channel settings : refers to the frequency bands used to transmit wireless data. Routers and wireless APs can choose the channel configuration, or it can be set manually if there is interference with another AP or wireless device.
Note : All routers and wireless APs must be protected with the highest available configuration. The None (WEP) or WEP options should be avoided, which should only be used in situations where security is not a cause for concern.
AP detection
Wireless devices must detect an AP or a wireless router and connect to it. Wireless clients connect to the AP through an analysis (polling) process. This process can be done in the following ways:- Passive mode : The AP openly announces its service by periodically sending broadcast signal frames containing the SSID, supported standards and security settings.
- Active mode : Wireless clients must know the name of the SSID. The wireless client starts the process by broadcasting a polling request frame on several channels. The polling request includes the name of the SSID and the supported standards.
If an AP or a wireless router is configured to not broadcast the signal frames, the active mode may be required.
How Active Mode AP works
Above figure shows how the passive mode works with the AP that broadcasts a signal frame with a certain frequency.
Above Image shows how active mode works with a wireless client that broadcasts a polling request for a specific SSID. The AP with that SSID responds with a polling response frame.
To discover nearby WLAN networks, a wireless client could also send a polling request without an SSID name .
APs configured to broadcast broadcast signal frames would respond to the wireless client with a polling response and provide the name of the SSID. The APs with the broadcast feature of the broadcast SSID disabled do not respond.
Authentication
The 802.11 standard was originally developed with two authentication mechanisms:- Open authentication : fundamentally, a NULL authentication where the wireless client says “authenticate me” and the AP answers “yes”. Open authentication provides wireless connectivity to any wireless device and should be used only in situations where security is not a concern.
- Shared key authentication : a technique that is based on a previously shared key between the client and the AP.
Wireless Authentication process
In above Image, a simple overview of the authentication process is provided. However, in most installations with shared key authentication, the exchange is as follows:
- The wireless client sends an authentication frame to the AP.
- The AP responds with a challenge text to the client.
- The client encrypts the message using the shared key and returns the encrypted text to the AP.
- Next, the AP decrypts the encrypted text using the shared key.
- If the decrypted text matches the challenge text, the AP authenticates the client. If the messages do not match the challenge text, the wireless client is not authenticated and wireless access is denied.
Wireless Association process
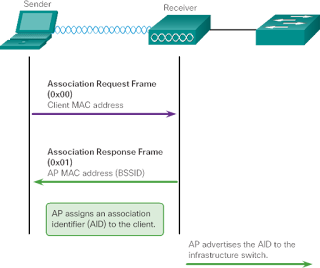
Once a wireless client was authenticated, the AP continues with the association stage. As shown in Image 12, the association stage completes the configuration and establishes the data link between the wireless client and the AP.As part of this stage:
- The wireless client forwards an association request frame that includes its MAC address.
- The AP responds with an association response that includes the BSSID of the AP, which is the MAC address of the AP.
- The AP assigns a logical port known as "association identifier" (AID) to the wireless client. The AID is equivalent to a port on a switch and allows the infrastructure switch to keep a record of the frames intended for the wireless client to resend.
- Once a wireless client is associated with an AP, traffic between the client and the AP can flow.
Next Related Post: Wireless Channel Management.





No comments:
Post a Comment