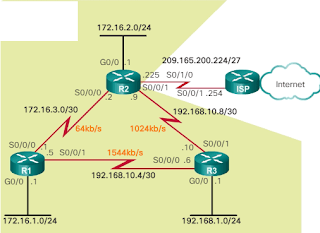
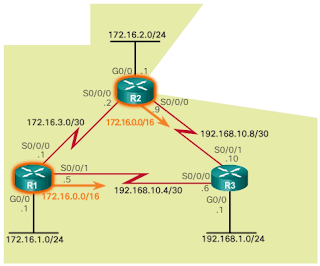
Types of WAN Technologies
This post provide you the different Type of WAN Technologies. You will learn about the different WAN Technologies like Leased lines, dial-up, ISDN, Frame Relay, ATM, WAN Ethernet, MPLS and VSAT. There are two main types of WAN Technologies:- Private WAN technologies
- Leased lines
- Dial-up
- ISDN
- Frame Relay
- ATM
- WAN Ethernet
- MPLS
- VSAT
- Public WAN Technologies
- DSL
- Cable WAN
- Wireless WAN
- 3G / 4G mobile data
- VPN technology
Private WAN Technologies
Following are the main type of Private WAN technologies:LEASED LINES
When permanent dedicated connections are required, a point-to-point link is used to provide a pre-established WAN communications path from the customer's facilities to the provider's network. Usually, a service provider leases the point-to-point lines, which are called " leased lines ."Leased lines exist since the early fifties and, for this reason, they are known by different names such as leased circuit, serial link, serial line, point-to-point link and line T1 / E1 or T3 / E3.
The term "leased line" refers to the fact that the organization pays a monthly lease fee to a service provider to use the line. There are leased lines available with different capacities and, generally, the price is based on the bandwidth required and the distance between the two connected points.
In North America, service providers use the carrier system T to define the digital transmission capacity of a serial link of copper media, while in Europe the carrier system E is used, as shown in the illustration. For example, a T1 link supports 1,544 Mb / s, an E1 supports 2,048 Mb / s, a T3 supports 43.7 Mb / s and an E3 connection supports 34,368 Mb / s. To define the digital transmission capacity of a fiber optic network, the transmission rates of the optical carrier (OC) are used.
ADVANTAGES OF LEASED LINES
The advantages of leased lines include the following:- Simplicity : point-to-point communication links require minimum installation and maintenance knowledge.
- Quality : point-to-point communication links generally offer high quality of service if they have adequate bandwidth. Dedicated capacity removes latency or vibration between terminals.
- Availability : constant availability is essential for some applications, such as electronic commerce. Point-to-point communication links provide the permanent dedicated capability that is needed for VoIP or for video over IP.
DISADVANTAGES OF LEASED LINES
Disadvantages of leased lines include the following:- Cost : In general, point-to-point links are the most expensive type of WAN access. When used to connect multiple sites over increasing distances, the cost of leased line solutions can be significant. In addition, each terminal requires an interface on the router, which increases equipment costs.
- Limited flexibility : WAN traffic is usually variable, and leased lines have a fixed capacity, so that the bandwidth of the line rarely matches the need accurately. Generally, any change in the leased line requires that ISP staff visit the site to adjust capacity.
- Generally, the layer 2 protocol is HDLC or PPP.
DIAL-UP
When no other WAN technology is available, dial-up WAN access may be required.For example, a remote location could use a modem and analog dial telephone lines to provide low capacity and dedicated switching connections. When low volume data transfers are required intermittently , dial-up access is convenient.
In traditional telephony, a copper wire is used, which is called a "local loop," to connect the telephone handset at the subscriber's premises to the CO. The signal in the local loop during a call is a continuously changing electronic signal, which is a translation of the subscriber's voice into an analog signal.
Traditional local loops can transport binary computer data through the voice telephone network using a modem. The modem modulates the binary data into an analog signal at the source and demodulates the analog signal into binary data at the destination. The physical characteristics of the local loop and its connection to the PSTN limit the signal speed to less than 56 kb / s.
For small businesses, these relatively low speed dial-up connections are suitable for exchanging sales figures, prices, regular reports and emails.
Using automatic dial-up at night or on weekends to transfer large files and back up data allows you to take advantage of lower non-peak hours (intercity charges). The rates depend on the distance between the terminals, the time of day and the duration of the call.
ADVANTAGES AND DISADVANTAGES OF DIAL-UP
The advantages of modems and analog lines are simplicity, availability and low cost of implementation. The disadvantages are low data speeds and a relatively long connection time. The dedicated circuit has little delay or little vibration for point-to-point traffic, but voice or video traffic does not work properly at these low bit rates.ISDN
The integrated services digital network (ISDN) is a circuit switching technology that enables the local loop of a PSTN to carry digital signals, resulting in higher capacity switching connections.ISDN changes the internal connections of the PSTN to transport time-division multiplexed digital signals (TDM) instead of analog signals. TDM allows two or more signals, or bit streams, to be transferred as subchannels in a communication channel. The signals seem to transfer simultaneously; however, physically, the signals take turns in the channel.
In Image, an example of an ISDN topology is shown. The ISDN connection may require a terminal adapter (TA), which is a device used to connect the ISDN basic speed interface (BRI) connections to a router.
ISDN converts the local loop into a TDM digital connection. This change allows the local loop to transport the digital signals, which generates higher capacity switching connections. The connection uses 64 kb / s carrier current (B) channels to carry voice and data, and a delta (D) signaling channel for call setup and other purposes.
TYPES OF ISDN INTERFACES
There are two types of ISDN interfaces:
- Basic Speed Interface (BRI) : The BRI ISDN is designed for use in homes and small businesses, and provides two 64 kb / s B channels and a 16 kb / s D channel. The BRI D channel is designed for control purposes and is often underused, because it only has to control two B channels.
BRI has a call setup time of less than one second, and the 64 kb / s B-channel provides greater capacity than an analog modem link. If more capacity is required, a second B channel can be activated to provide a total of 128 kb / s. While it is not suitable for video, it allows several simultaneous voice conversations in addition to data traffic.
- Primary Speed Interface (PRI) : ISDN is also available for larger installations. In North America, PRI provides 23 B channels with 64 kb / s and a D channel with 64 kb / s for a total bit rate of up to 1,544 Mb / s. This includes some additional overhead for synchronization. In Europe, Australia and other parts of the world, PRI ISDN provides 30 B channels and one D channel for a total bit rate of up to 2,048 Mb / s, which includes the overhead for synchronization.
With PRI ISDN , several B channels can be connected between two terminals. This allows video conferencing and data connections with high bandwidth without latency or vibration. However, using several connections over long distances can be very expensive.
FRAME RELAY
Frame Relay is a simple Layer 2 multi-access WAN technology (NBMA) that is used to interconnect a company's LAN .To connect to several sites using PVC, a single router interface can be used. PVCs are used to transport voice and data traffic between source and destination and support data speeds of up to 4 Mb / s, although some providers offer even higher speeds.
Perimeter routers only require a single interface, even when multiple virtual circuits (VC) are used. The leased line cuts to the perimeter of the Frame Relay network allows cost-effective connections between widely dispersed LANs.
Frame Relay creates PVCs that are identified only by a data link connection identifier (DLCI). PVCs and DLCIs ensure bidirectional communication from one DTE device to another.
For example, in Image, R1 uses DLCI 102 to reach R2, while R2 uses DLCI 201 to reach R1.
ATM Asynchronous Transfer Mode
Asynchronous transfer mode (ATM) technology can transfer voice, video and data through private and public networks. It is built on a cell-based architecture, rather than a frame-based architecture. ATM cells always have a fixed length of 53 bytes. The ATM cell contains a 5-byte ATM header, followed by 48 bytes of ATM content. Small and fixed-length cells are suitable for transporting voice and video traffic, because this type of traffic does not support delays. Voice and video traffic do not have to wait for larger data packets to be transmitted.The 53-byte ATM cell is less efficient than larger Frame Relay frames and packets. In addition, the ATM cell has at least 5 bytes of overhead for each 48-byte content.
When the cell transports segmented network layer packets, the overhead is greater because the ATM switch must be able to reset packets at the destination. A typical ATM line needs almost 20% more bandwidth than Frame Relay to transport the same volume of network layer data.
ATM was designed to be extremely scalable and to support link speeds from T1 / E1 to OC-12 (622 Mb / s) and more.
ATM offers PVC and SVC , although PVC is more common with WANs. As with other sharing technologies, ATM allows several VCs in a single leased line connection to the perimeter of the network.
WAN ETHERNET
Originally, Ethernet was developed to be a LAN access technology. However, at that time it was not really suitable as WAN access technology, because the maximum allowed cable length was only up to one kilometer.However, the latest Ethernet standards using fiber optic cables made Ethernet a reasonable WAN access option. For example, the IEEE 1000BASE-LX standard supports fiber optic cable lengths of 5 km, while the IEEE 1000BASE-ZX standard supports cable lengths of up to 70 km.
Now, service providers offer WAN Ethernet service with fiber optic cabling. The WAN Ethernet service can be known by different names, including Metropolitan Ethernet (MetroE), Ethernet by MPLS (EoMPLS) and the Virtual Private LAN (VPLS) service.
The benefits of WAN Ethernet include the following:
- Cost and administration reduction : WAN Ethernet provides a layer 2 switching network with high bandwidth that is capable of managing data, voice and video in the same infrastructure.
- Easy integration with existing networks : WAN Ethernet easily connects to existing Ethernet LANs, reducing costs and installation time.
- Enhanced company productivity : WAN Ethernet allows companies to leverage IP applications to improve productivity, such as hosted IP communications, VoIP and video transmission and broadcasting, which are difficult to implement in TDM or Frame Relay networks.
MPLS
Multi-protocol tag switching (MPLS) is a high-performance multi-protocol WAN technology that directs data from one router to the next according to short path tags , rather than IP network addresses.MPLS has several characteristics that define it. It is multiprotocol, which means it has the ability to transport any content, including IPv4, IPv6, Ethernet, ATM, DSL and Frame Relay traffic. Use tags that tell the router what to do with a package. The tags identify the routes between remote routers — instead of between terminals — and while MPLS routes IPv4 and IPv6 packets effectively, everything else is switched.
MPLS is a service provider technology . Leased lines deliver bits between sites, and Frame Relay and WAN Ethernet deliver frames between sites. However, MPLS can deliver any type of package between sites.
MPLS can encapsulate packets of various network protocols. It supports a wide variety of WAN technologies, including T and E carrier links, Carrier Ethernet, ATM, Frame Relay and DSL.
In the example of topology in Image 9, it is shown how MPLS is used. Note that different sites can connect to the MPLS cloud using different access technologies. In the illustration, CE refers to the customer's perimeter, PE is the perimeter router of the provider that adds and removes tags, and P is an internal router of the provider that switches packets with MPLS tags.
VSAT
In all the private WAN technologies analyzed so far, copper or fiber optic media are used. What would happen if an organization needed connectivity in a remote location where there were no service providers offering a WAN service?A very small opening terminal (VSAT) is a solution that creates a private WAN through satellite communications . A VSAT is a small satellite dish similar to those used for Internet and home television. VSATs create a private WAN while providing connectivity to remote locations.
Specifically, a router connects to a satellite dish that points to a service provider's satellite in a geosynchronous orbit in space. The signals must travel around 35,786 km (22,236 mi) to the satellite and return.
In the example in Image, a VSAT antenna is shown on the roofs of the buildings, which communicates with a satellite dish thousands of kilometers away in space.
Public WAN Technologies
This section compares the different public WAN technologies : DSL, cable, wireless technology and 3G / 4G mobile data. In addition to security with private virtual networks (VPN).DSL
DSL technology is a permanent connection technology that uses existing twisted pair telephone lines to transport data with high bandwidth and provides subscriber IP services.A DSL modem converts an Ethernet signal from the user device into a DSL signal, which is transmitted to the central office.
Several DSL subscriber lines are multiplexed into a single high capacity link using a DSL access multiplexer (DSLAM) at the provider's location. DSLAMs incorporate TDM technology for aggregation of several subscriber lines on a single medium, usually a T3 (DS3) connection. To achieve fast data rates, current DSL technologies use sophisticated coding and modulation techniques.
There is a wide variety of types, standards and emerging DSL standards. Currently, DSL is a popular option for the provision of support to homeworkers by corporate IT departments.
Generally, a subscriber cannot choose to connect to a business network directly, but must first connect to an ISP and then an IP connection to the company is made over the Internet. Security risks are generated in this process, but they can be remedied with security measures.
CABLE WAN Technology
In urban areas, coaxial cable is widely used to distribute television signals. Many cable television providers offer network access. This allows a bandwidth greater than the local conventional telephony loop.Cable modems provide a permanent connection and have a simple installation. A subscriber connects a computer or a LAN router to the cable modem, which translates the digital signals by broadband frequencies that are used for transmission on a cable television network.
The local cable television office, which is called a “ cable header, ” contains the computer system and databases that are needed to provide Internet access. The most important component located in the header is the cable modem termination system (CMTS), which sends and receives digital cable modem signals in a cable network and is required to provide Internet services to subscribers.
Cable modem subscribers must use the ISP associated with the service provider. All local subscribers share the same cable bandwidth. As more users join the service, the available bandwidth may be below the expected speed.
WIRELESS WAN
To send and receive data, wireless WAN technology uses the radio spectrum without a license. Anyone who has a wireless router and wireless technology on the device they use can access the spectrum without a license.Until recently, a limitation of wireless access was the need to be within the local transmission range (usually less than 100 ft [30 m]) of a wireless router or a wireless modem with a wired Internet connection . The following advances in wireless broadband technology are changing this situation:
- MUNICIPAL WI-FI
Many cities began installing municipal wireless networks. Some of these networks provide high-speed Internet access for free or for a price substantially lower than other broadband services. Others are only for the use of the city administration and allow police, firefighters and other municipal employees to perform certain aspects of their work remotely.
To connect to municipal Wi-Fi, a subscriber usually needs a wireless modem, which provides a more powerful radio and directional antenna than conventional wireless adapters. Most service providers provide the necessary equipment for free or for a fee, similar to what happens with DSL modems or cable modems.
- WIMAX
Global interoperability for microwave access (WiMAX) is a new technology that has just begun to be used. It is described in the IEEE 802.16 standard.
WiMAX provides a high-speed broadband service with wireless access and provides extensive coverage such as a cellular telephone network, rather than small areas of Wi-Fi wireless coverage.
WiMAX works similarly to Wi-Fi, but with higher speeds, over longer distances and for a greater number of users.
Use a network of WiMAX towers that are similar to cell phone towers. To access a WiMAX network, subscribers must subscribe to an ISP with a WiMAX tower within 30 mi (48 km) of its location. To access the base station, they also need some type of WiMAX receiver and a special encryption code.
- SATELLITE INTERNET
Generally used by users in rural areas, where there is no cable or DSL. A VSAT provides two-way data communications (upload and download).
The upload speed is approximately one tenth of the download speed of 500 kb / s. Cable and DSL have higher download speeds, but satellite systems are about ten times faster than an analog modem.
To access satellite Internet services, subscribers need a satellite dish, two modems (uplink and downlink) and coaxial cables between the antenna and the modem.
3G / 4G MOBILE DATA
Increasingly, cellular service is another wireless WAN technology used to connect users and remote locations where no other WAN access technology is available.Phones, tablet PCs, laptops and even some routers can communicate over the Internet using mobile data technology. These devices use radio waves to communicate through a mobile phone tower . The device has a small radio antenna, and the provider has a much larger antenna that is located at the top of a tower somewhere at a certain distance from the phone.
Some common terms of the mobile data industry include the following:
- 3G / 4G wireless : abbreviation for third and fourth generation cellular access. These technologies support wireless Internet access.
- Long-term evolution (LTE) : refers to a newer and faster technology, which is considered part of the fourth generation (4G) technology.
VPN TECHNOLOGY
When a remote worker or a worker in a remote office uses broadband services to access the corporate WAN through the Internet, security risks are generated. To address security issues, broadband services provide capabilities to use VPN connections to a VPN server , which is usually located on the corporate site.A VPN is an encrypted connection between private networks through a public network, such as the Internet. Instead of using a dedicated Layer 2 connection, such as a leased line, a VPN uses virtual connections called “ VPN tunnels ,” which are routed over the Internet from the company's private network to the site host or the remote employee. .
VPN BENEFITS
VPN benefits include the following:- Cost savings : VPNs allow organizations to use the global Internet to connect remote offices and users to the main corporate site, eliminating the need for dedicated WAN links and expensive modem banks.
- Security : VPNs provide the maximum level of security through two advanced encryption and authentication protocols that protect data from unauthorized access.
- Scalability : Because VPNs use the Internet infrastructure in ISPs and devices, it is easy to add new users. Companies can greatly increase capacity, without adding significant infrastructure.
- Compatibility with broadband technology : Broadband service providers, such as DSL and cable, support VPN technology, so that mobile workers and remote employees can take advantage of their homes' high-speed Internet service to Access corporate networks.